CI/CD pipelines to close the circle
In this chapter you’re going to deploy CI and CD pipelines based on tekton that will help to automate the processes of continuos integration and delivery. It’s made of three sections, the first one deploys an ArgoCD Application that will create not only the pipelines but all the necessary elements the other two will guide you to generate the secrets necessary to connect to the git repos and the container image registry.
| It’s a best practice avoid storing secrets in a git repository even if it’s private. There are several ways to deal with secrets in this kind of scenarios but in this case we’re going to manage them manually for the sake of simplicity. |
Deploying CICD Pipelines
We are going to deploy another ArgoCD application, this time to deploy pipelines. Please run this command which will create an ApplicationSet to deploy our CICD pipelines.
cat <<EOF | oc apply -n openshift-gitops -f -
apiVersion: argoproj.io/v1alpha1
kind: ApplicationSet
metadata:
name: kitchensink-cicd-%USERNAME%
namespace: openshift-gitops
labels:
kitchensink-cicd-appset: "true"
spec:
generators:
- list:
elements:
- cluster: in-cluster
ns: "cicd-tekton-%USERNAME%"
template:
metadata:
name: kitchensink-cicd-%USERNAME%
namespace: openshift-gitops
labels:
kitchensink-cicd-app: "true"
finalizers:
- resources-finalizer.argocd.argoproj.io
spec:
destination:
namespace: '{{ ns }}'
name: '{{ cluster }}'
project: default
syncPolicy:
automated:
selfHeal: true
source:
helm:
parameters:
- name: kitchensinkRepoUrl
value: "https://repository-gitea-system.apps.%BASE_SUBDOMAIN%/%USERNAME%/kitchensink"
- name: kitchensinkRevision
value: "main"
- name: kitchensinkConfRepoUrl
value: "https://repository-gitea-system.apps.%BASE_SUBDOMAIN%/%USERNAME%/kitchensink-conf"
- name: kitchensinkConfRevision
value: "main"
- name: username
value: "%USERNAME%"
- name: gitSslVerify
value: "true"
- name: cicdNamespace
value: "cicd-tekton-%USERNAME%"
- name: overlayDevNamespace
value: "helm-kustomize-dev-%USERNAME%"
- name: overlayTestNamespace
value: "helm-kustomize-test-%USERNAME%"
- name: containerRegistryServer
value: myregistry-quay-quay-system.apps.%BASE_SUBDOMAIN%
- name: containerRegistryOrg
value: %USERNAME%
path: cicd
repoURL: "https://repository-gitea-system.apps.%BASE_SUBDOMAIN%/%USERNAME%/kitchensink-conf"
targetRevision: main
EOFLet’s go to ArgoCD console and see how it’s going on. Please copy the next link and open it in a new tab.
https://openshift-gitops-server-openshift-gitops.apps.%BASE_SUBDOMAIN%/applications?proj=&sync=&health=&namespace=&cluster=&labels=kitchensink-cicd-app&search=%USERNAME%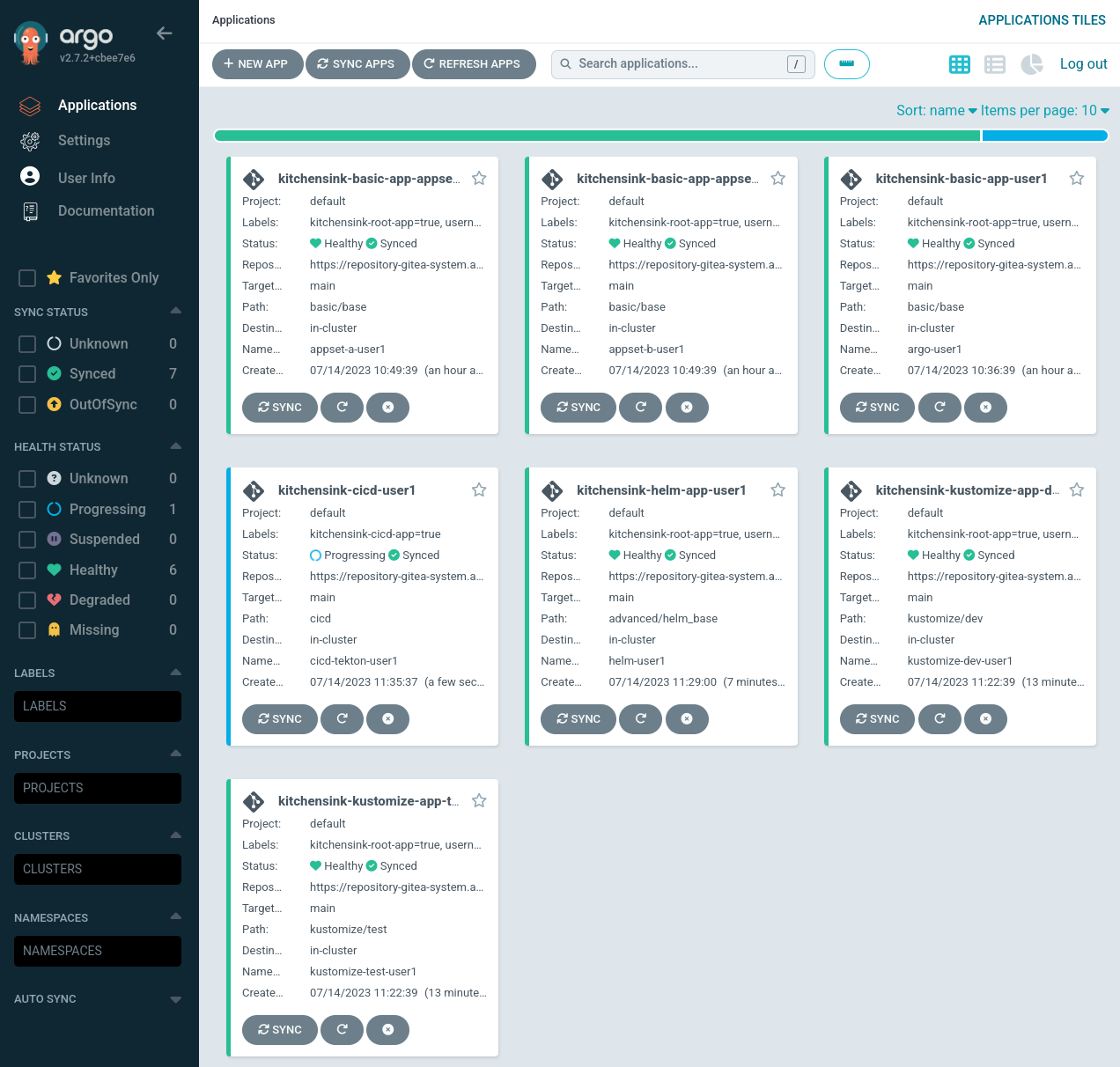
And go deeper by clicking on the Application object or using the next link.
https://openshift-gitops-server-openshift-gitops.apps.%BASE_SUBDOMAIN%/applications/kitchensink-cicd-%USERNAME%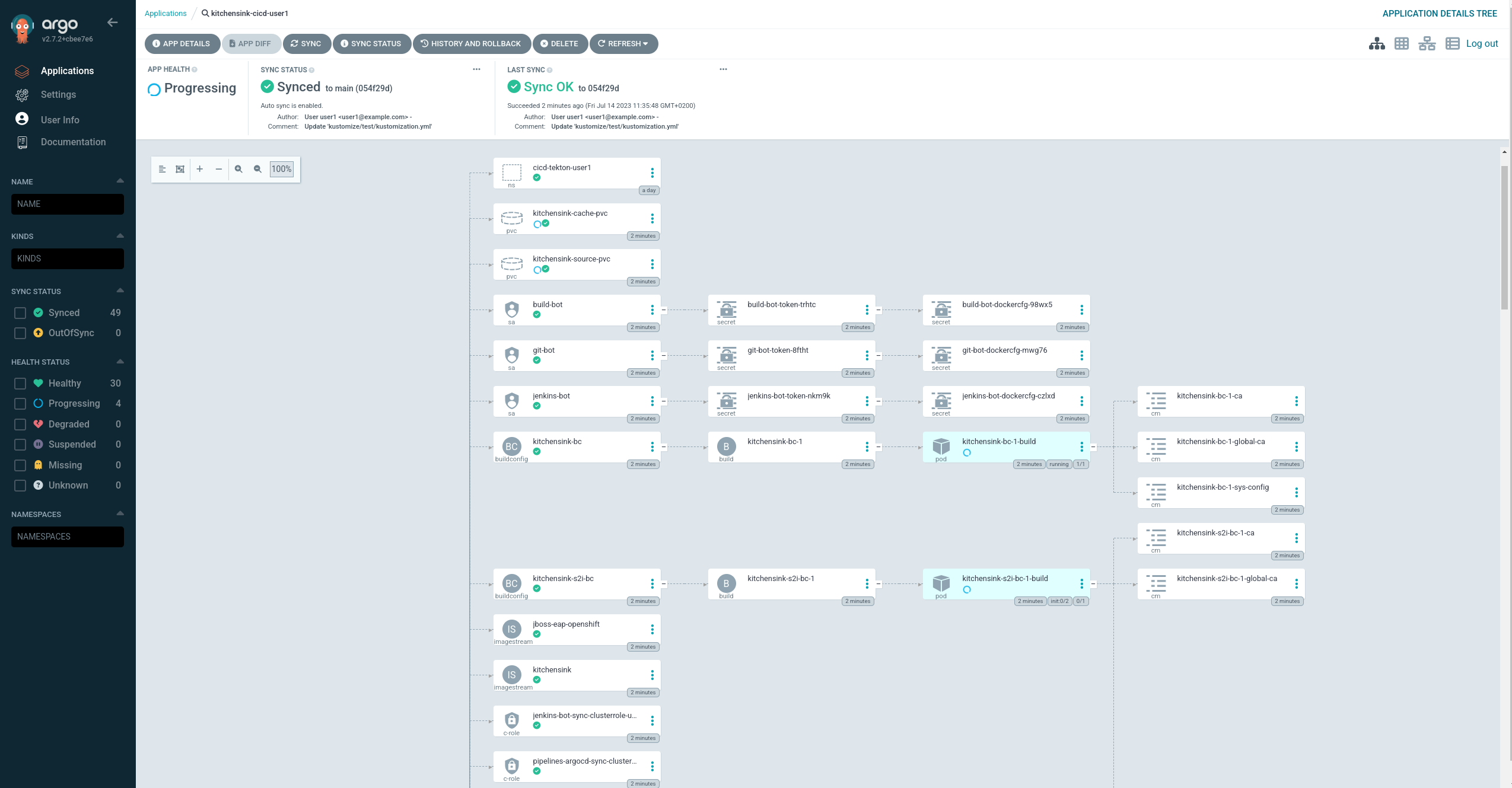
You can also have a look to the pipelines created in the OpenShift web console.
https://console-openshift-console.apps.%BASE_SUBDOMAIN%/dev-pipelines/ns/cicd-tekton-%USERNAME%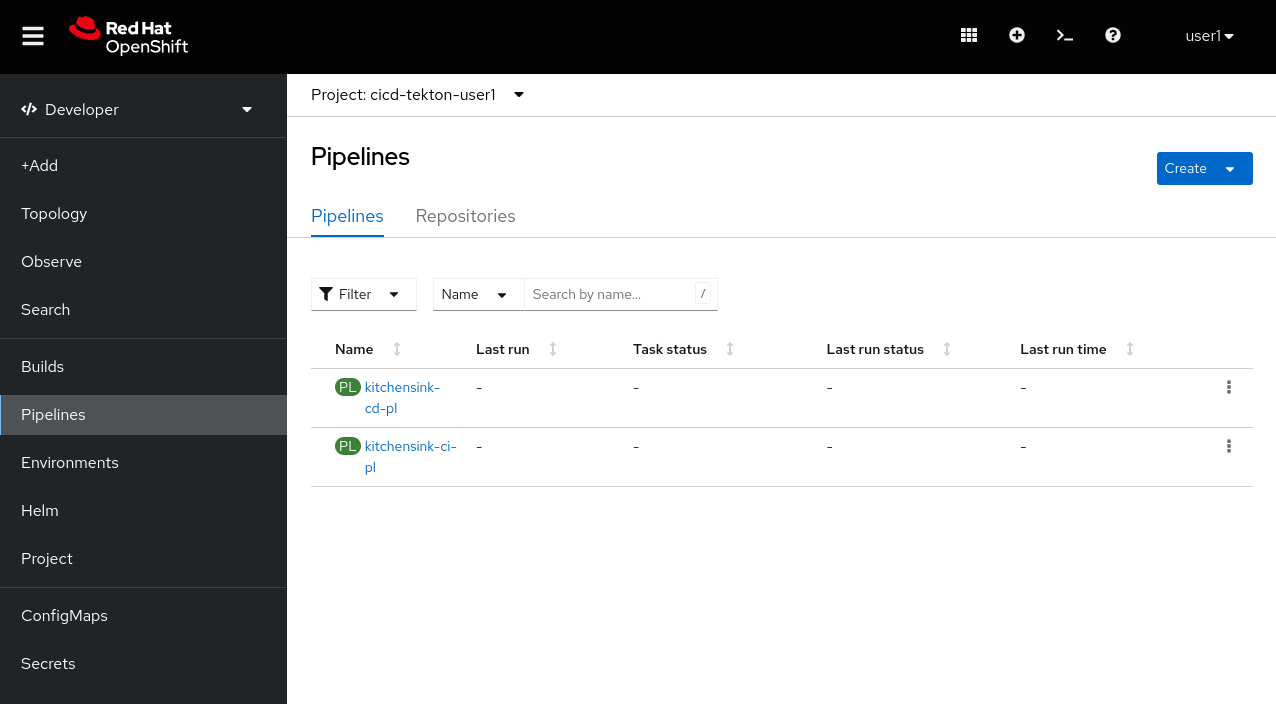
Create Git Secret
We are going to create secrets instead of storing them in the git repo, but before we do that let’s check that ArgoCD has created the namespace for us.
|
If the namespace is not there yet, you can check the sync status of the ArgoCD application with: |
oc get project cicd-tekton-%USERNAME%You should see something like this:
NAME DISPLAY NAME STATUS
cicd-tekton-user1 ActiveFine, the namespace is in place, it’s time to create the git secret our pipelines will use when cloning and also while creating Pull Requests which are the fuel for the CD part of the pipelines to promote from one environment to the next.
Let’s create a PAT here, don’t worry if you created one before.
|
You can run this command as often as needed |
GIT_PAT=$(curl -k -s -XPOST -H "Content-Type: application/json" \
-d '{"name":"cicd'"${RANDOM}"'","scopes": ["repo"]}' \
-u %USERNAME%:openshift \
https://repository-gitea-system.apps.%BASE_SUBDOMAIN%/api/v1/users/%USERNAME%/tokens | jq -r .sha1)
echo "GIT_PAT=${GIT_PAT}"Create the actual secret which embeds the PAT you just created using the next command:
cat <<EOF | oc apply -n cicd-tekton-%USERNAME% -f -
apiVersion: v1
kind: Secret
metadata:
name: git-pat-secret
namespace: cicd-tekton-%USERNAME%
type: kubernetes.io/basic-auth
stringData:
user.name: %USERNAME%
user.email: "%USERNAME%@example.com"
username: %USERNAME%
password: ${GIT_PAT}
EOFYou have to annotate the secret so that it can actually be used by the pipeline.
oc annotate -n cicd-tekton-%USERNAME% secret git-pat-secret \
"tekton.dev/git-0=https://repository-gitea-system.apps.%BASE_SUBDOMAIN%"Now that the secret is in place and annotated you can proceed to the next chapter.